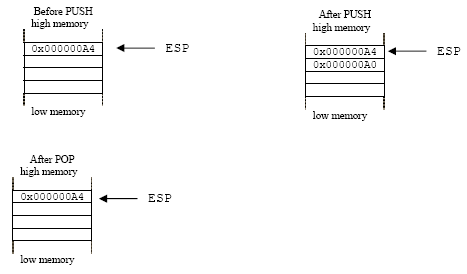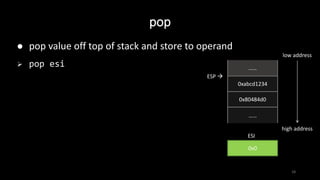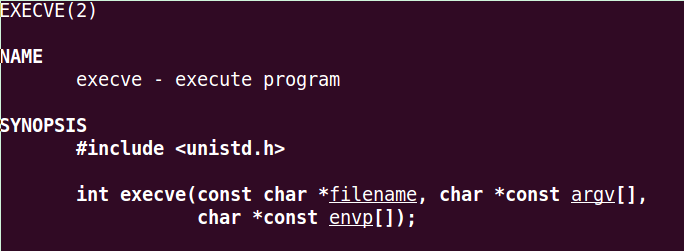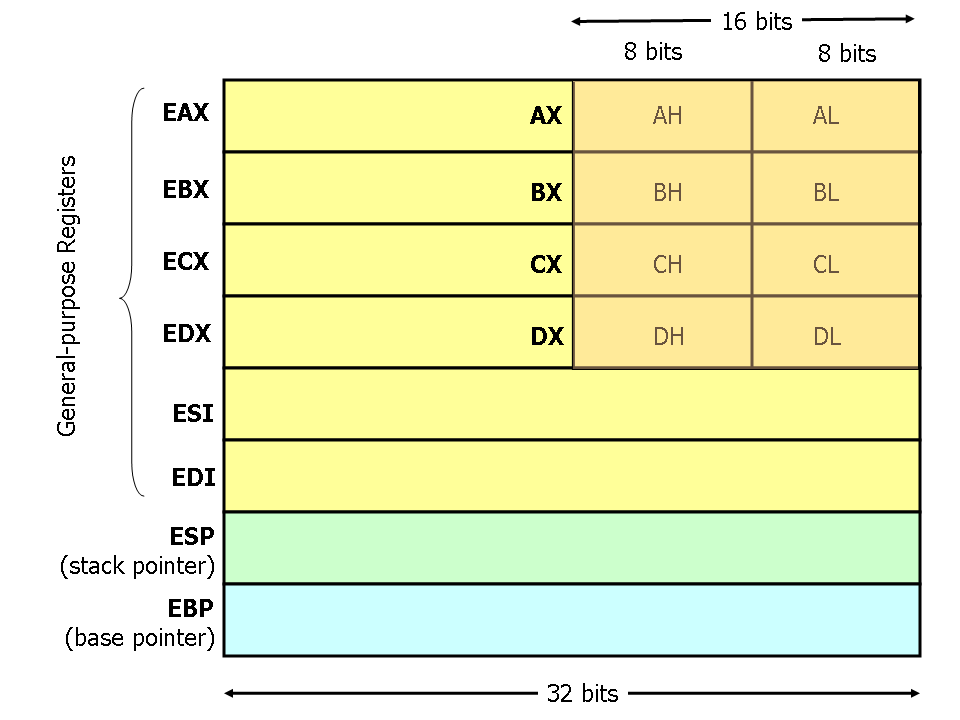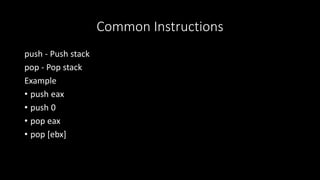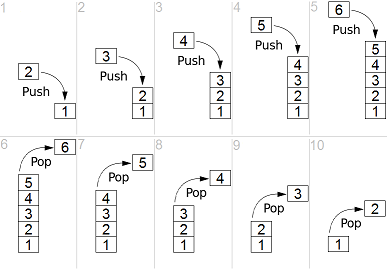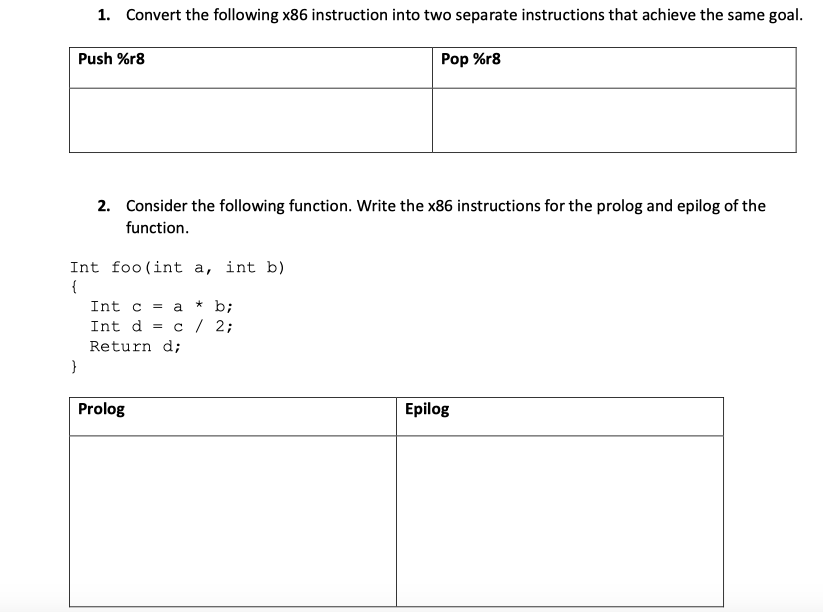
1 Convert Following X86 Instruction Two Separate Instructions Achieve Goal Push 9gr8 Pop 8 Q37224177 - Answer Streak
Writing Your First x86 Program. X86 is an assembly programming language… | by Scott Cosentino | Medium
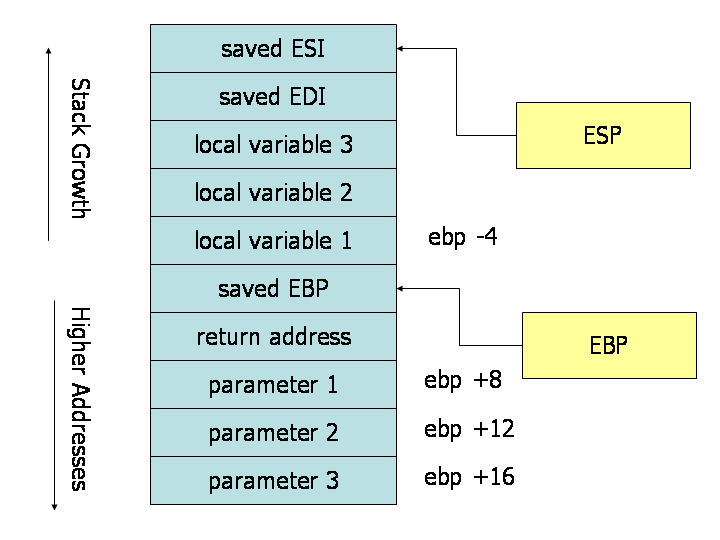
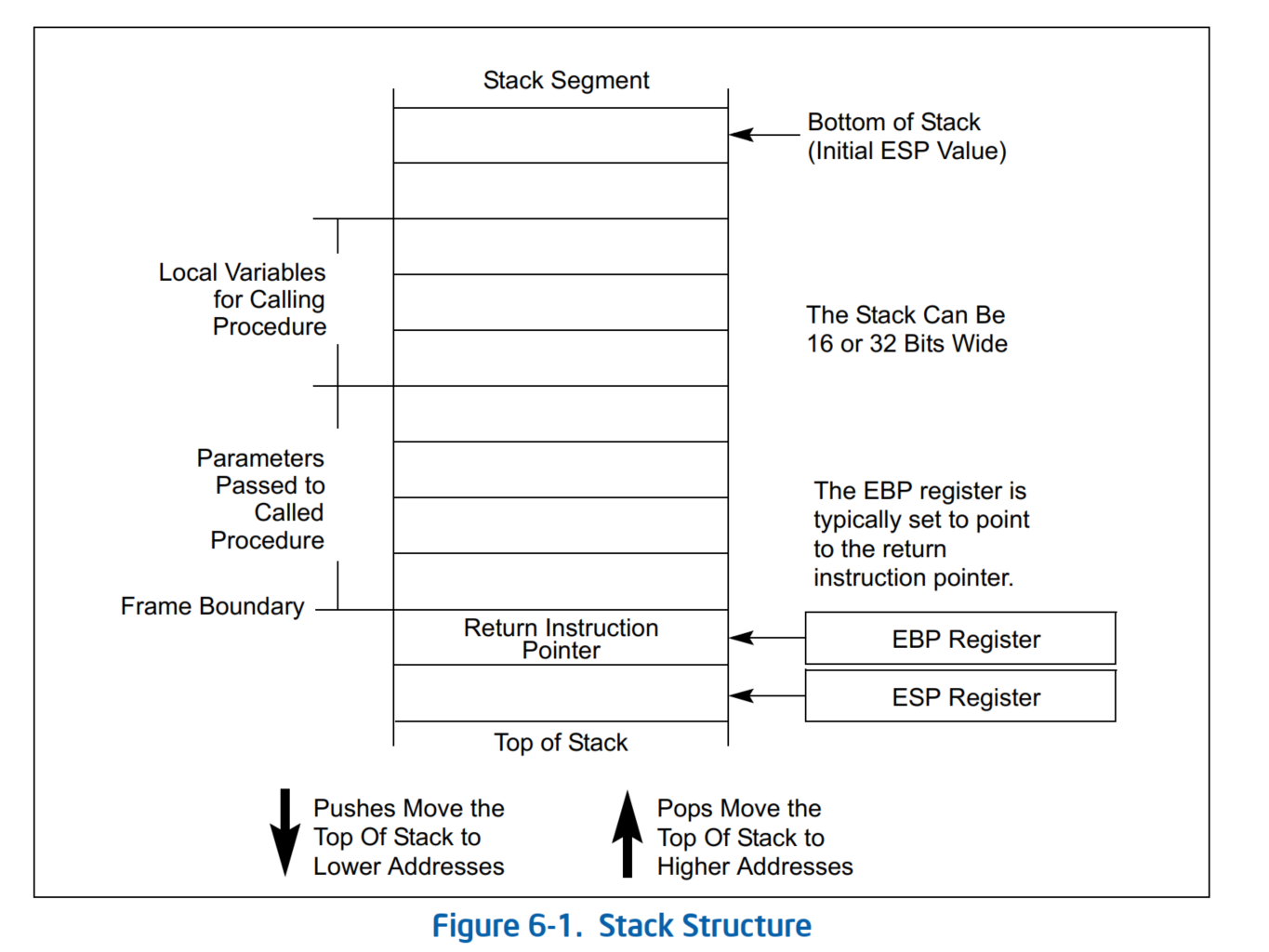
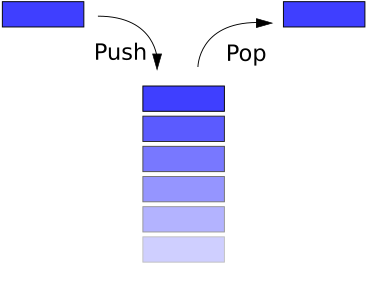
Outline The stack Push and pop instructions Offset-based stack accesses Argument and return registers Sharing registers Preservi

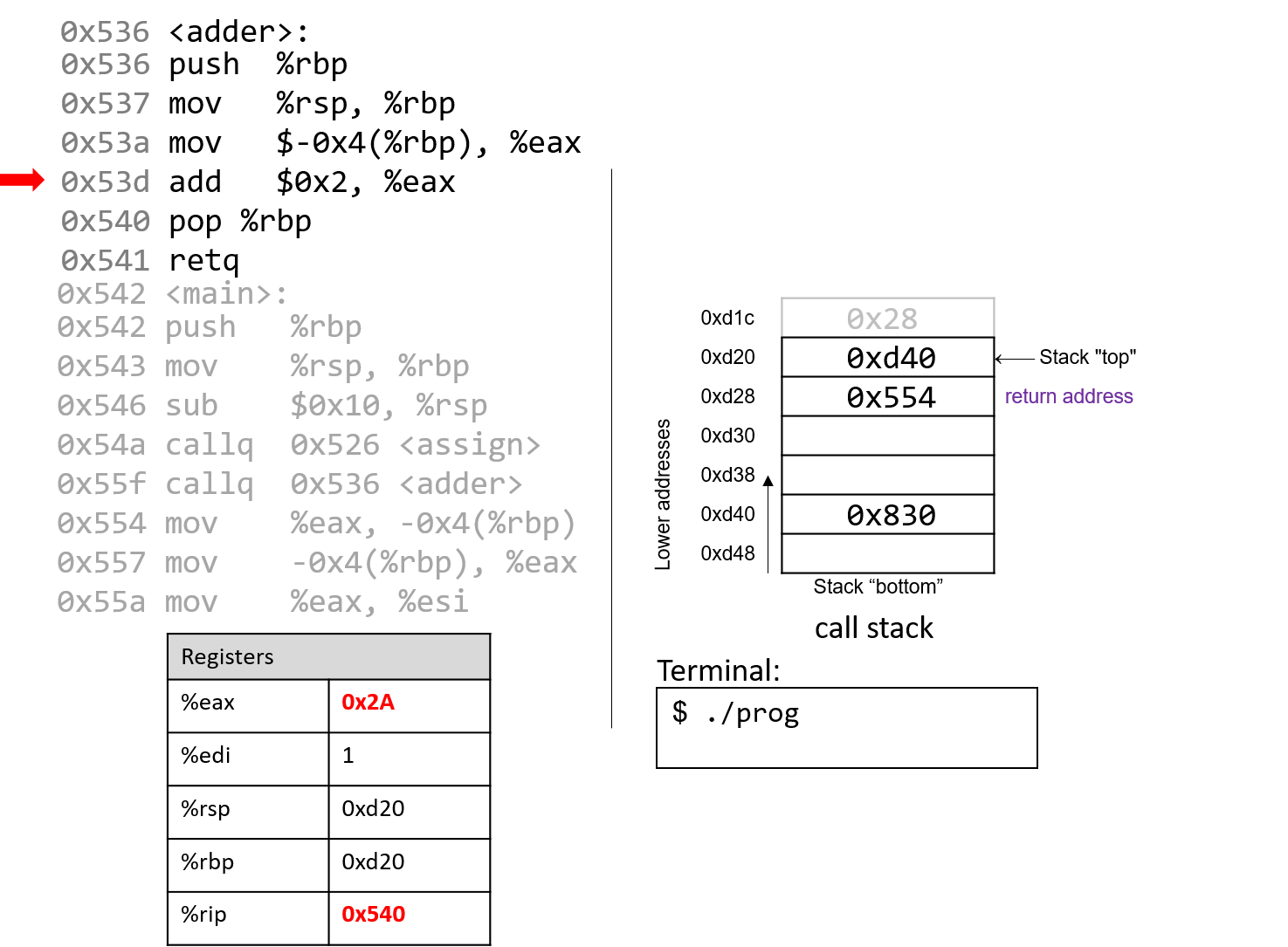
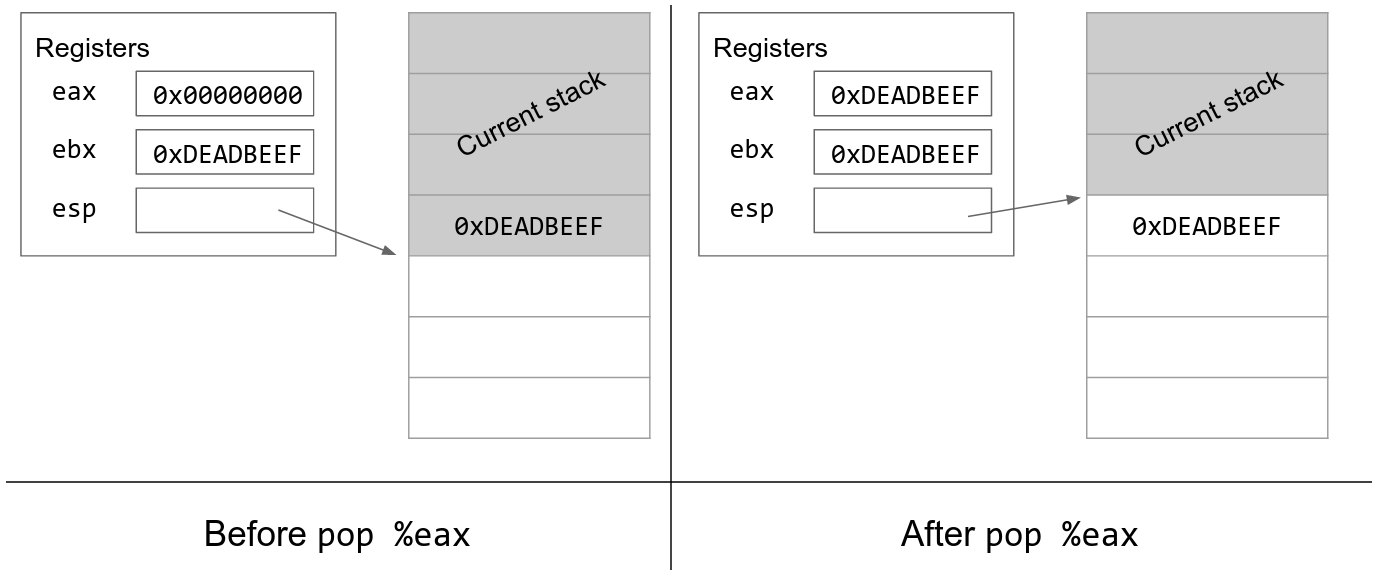
x86 - What happens exactly under the hood to Assembly `push`, `pop`, `call`, and `ret` operations? - Stack Overflow

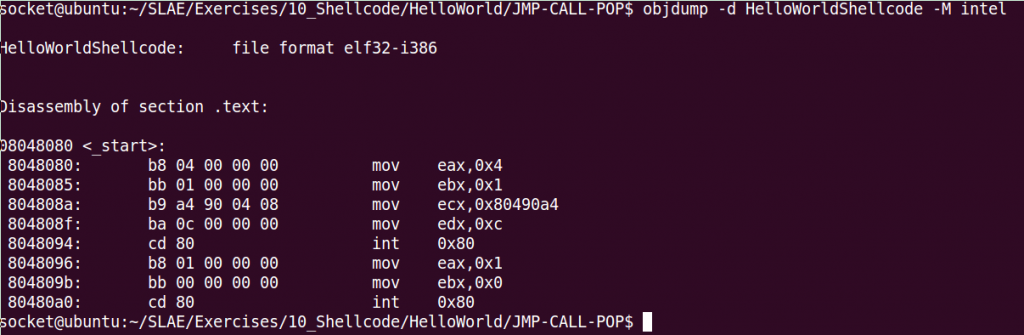
winapi - What is the purpose of the pause x86 instruction and the loop in the GetSystemTimeAsFileTime function disassembly? - Stack Overflow